This article will cover different techniques you can use to secure your computer from malware and unwanted security leaks. By the end of this article you will be equipped with the skills to verify that what you are getting is what you want. You won’t have to be paranoid about downloading malware anywhere. This is great for anyone who uses cryptocurrencies on their native computer. As most cryptocurrency software is a target for hackers.
In order to explain these techniques, we will walk through the process and you can follow along if you’re a hands-on learner.
Anything we download on the internet has the potential to expand our systems functionality whilst also exposing us to harmful unwanted side effects (malware, virus, trojans etc.)
Thus, we must be extremely conscious of the software we decide to use.
For most of this article we will be using the Brave browser software as an example. But the processes we will apply here can be applied to all other software.
The first question we need to ask ourselves is, do we need this software?
The Brave browser software is in my opinion far better than Google Chrome, Firefox and all the other browsers I have used over the years. Of course, I didn’t know that until I actually used it.
However, I am currently on a Mac and by default the browser is Safari. Which has its benefits. But I needed a browser that would give me access to browser extensions and Safari doesn’t have that capability. So yes, I need this software.
The second question is, is this software company trustworthy?
Determining this is not always straightforward, but there are a few things you can look at.
We can look at the social proof of software.
This can be done by checking social media accounts, google search results, youtube reviews. Anything that relates to its social acceptance should give a good indication that it’s used by lots of people.
Brave even has a transparency report right on their webpage. Now that’s first class! Would love to see more companies do this.
Open Source
Open source means that the code is available online for anyone to review. This way the developers can’t launch a product with spyware built in. Of course, not all software will be open source, because that would mean anyone can also copy the software. You probably won’t find any open source software that is paid.
Lucky for us, Brave is open-source software. I found this link by checking their FAQ.
Reviews
If you can’t find much information on the software in question and you really need it, you can always look for reviews. Search “[Software Name] scam” and “[Software Name] Reviews”. The first query should give you a good indication of whether to avoid or not. The second should provide some more social proof.
The third question. Am I downloading the right software?
Popular software will often be a target for scammers. They will create lookalike webpages and software packages in order to get you to download the wrong software.
To avoid this.
- Always download the software from the official website
- Don’t use pirated software
- Don’t download from a third party software site (ie. download.net)
The fourth question. Has this software been tampered with?
At this point we have determined the software in question is worth downloading and we are downloading from the official source.
Ok, if you’re super paranoid about downloading anything to your device you can always download the software to a virtual box and monitor the network connections and file changes when you run it, but that goes beyond the scope of this article. I personally don’t do this because it doesn’t make a difference to my threat model. If I was running a multi-million dollar business with unsecured information/assets being processed by myself and various employees on a common network, I might be more inclined to take this route. There are always tradeoffs in security and ease of use. So this is a step I will skip.
So let’s go ahead and download Brave from the official website.
Oh wait a second… We are missing a step here.
Ok. Well, I was really expecting Brave to have Binaries and deterministic signatures included in the download. (I’ll get to what those are in a moment). They don’t have signatures anywhere so unfortunately, I can’t check the authenticity of this download. This is a yellow flag, so proceed with caution and make sure you are at least downloading software over a secure https connection. An issue has been filed in their Github here. Apparently, it’s not a simple task for them to include these signatures, so I’ll let this slide. But I think this is a good example, because you won’t always find signatures included with software and typically you will want to stay away if you can.
So for completeness of this article I will shift our example to Ledger software.
Since this is somewhat of a crypto related article, I imagine many of you will also be using hardware wallets. YOU SHOULD BE. Ledger is a popular one. I prefer Trezor because they are open source, but they don’t support as many coins. So I use both. I digress.
I’ve already vetted the Ledger company website and I am ready to download.
Here is their current download page.
At first glance it doesn’t look like they have included the download signatures here either, but you gotta go looking for them. Why does security have to be hard?
On the same page I scrolled down and found this.
YES. We want the release & binary. Click that link and it will bring you here.
This is what I was looking for on the Brave website, but unfortunately was unable to find it.
What is a hash?
The hash/signature is basically the unique fingerprint of a software package.
Every time a new version of software is released it gets a new fingerprint that uniquely identifies that software. It’s usually included with software downloads so users can verify the software hasn’t been tampered with.
The problem with these signatures is that most users have no idea what they are, nor how they are used. That’s what I’ll be covering now.
This part of the article is really the reason why I wrote this article. The aforementioned parts should be common sense for most of you, or at least it does not require any technical skill. But I included it for completeness.
Download
Let’s click that download button now.
Remember where you save the file too, we will need that location in the next step.
DO NOT DOUBLE CLICK AND RUN THE INSTALLER!! Yet…
You should now have a .dmg file or .exe or .AppImage file depending on your Operating System.
Now the fun part.
- We have to open up our command line tool. I’m on a mac so this is the Terminal.
- Next we navigate to the folder where we downloaded the installer. For me that was the Desktop. Many of you might also have a Downloads folder. If you have trouble navigating inside the command line, watch a youtube video or something on how to change directories. Once we are in the right directory you can copy and paste the rest of the commands.
- 2a. If you are really having trouble navigating you can just manually drag and drop the installer into the current working directory. You can figure out the current working directory by using the `pwd` command.
- So we are in the directory where our installer is located. You can verify this by using the `ls` command.
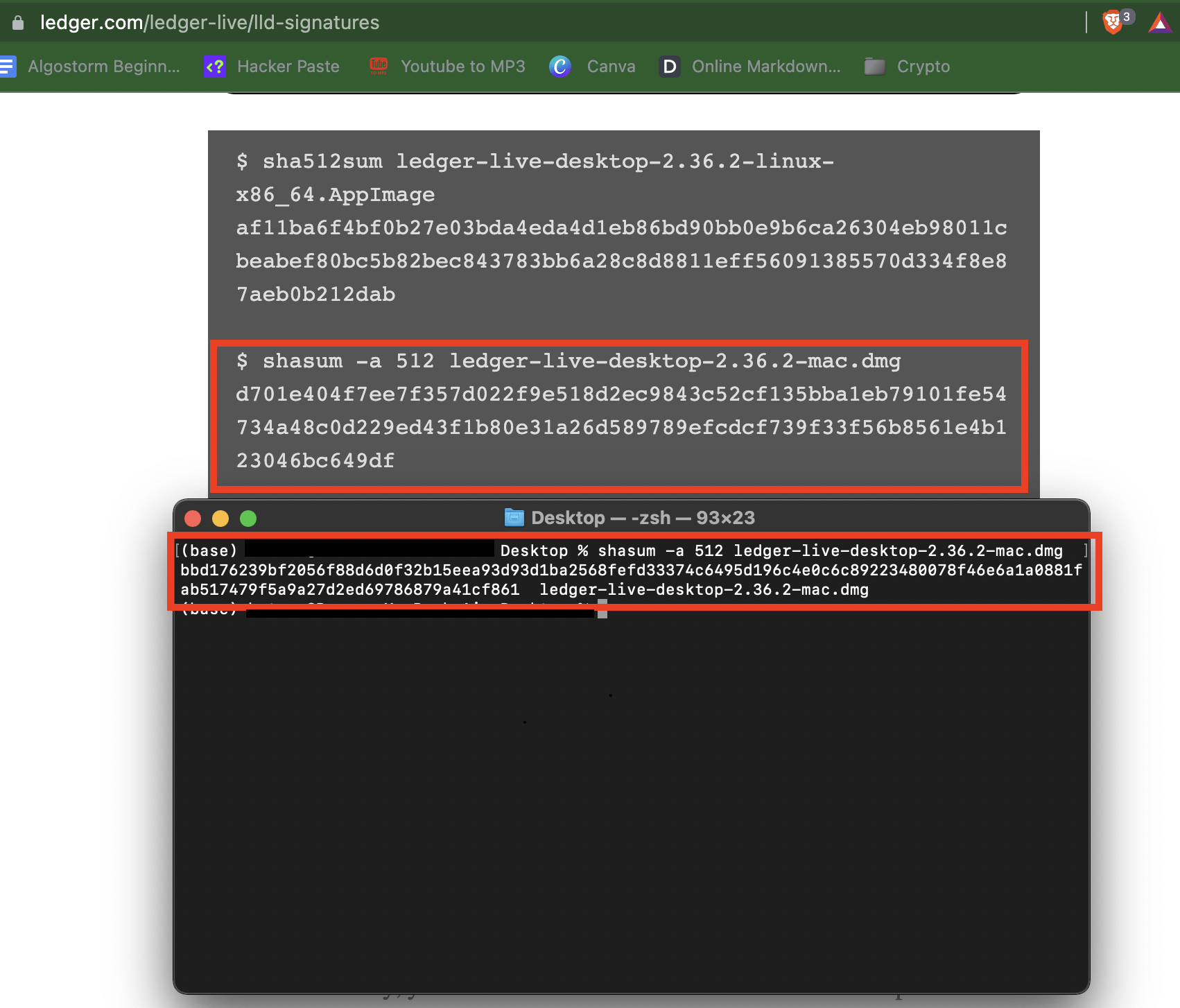
- Now let’s go back to the signatures page and copy the code that corresponds to our download.
Mac: shasum -a 512 [NameOfFile]
Windows: Get-FileHash [NameOfFile] -Algorithm SHA5121
There is also CertUtils for windows. You can read more about that process here.
Remember that you can use this command on any file you choose. So keep in mind the commands, because you will need to use them for everything you download in the future.
- Run the command.
After running the command, you should get a bunch of numbers and letters. That is the signature. Now all we have to do is navigate back to the original web page and verify that this signature matches the one that was posted.
- Verify the signatures match.
THESE SIGNATURES DO NOT MATCH!
Uh oh. - Delete that shit, report it to help others. You can look for an older version to download or wait until the website fixes the security issue.
- Usually the signatures match. At that point you can either verify it across other available signatures. There is a few different formats (MD5, SHA256, PGP, MD1)
Or… you can call it good and run the installer.
That’s it! Looks like we weren’t exactly successful. But we successfully avoided installing contaminated software onto our personal computers. Stay safe out there! 🙂